Detailed Questions and Explanations asked in all Slots of SBI PO Prelims Exam held on April 29, 2017 (Memory based)
Want to Become a Bank, Central / State Govt Officer in 2020?
Join the Most awarded Coaching Institute & Get your Dream Job


Now Prepare for Bank, SSC Exams from Home. Join Online Coure @ lowest fee
Lifetime validity Bank Exam Coaching | Bank PO / Clerk Coaching | Bank SO Exam Coaching | All-in-One SSC Exam Coaching | RRB Railway Exam Coaching | TNPSC Exam Coaching | KPSC Exam Coaching
Detailed Questions and Explanations asked in all Slots of SBI PO Prelims Exam held on April 29, 2017 (Memory based)
Questions asked in Slot 1
- Russia has deployed attack and transport helicopters to reinforce its military base in Armenia, RIA news agency quoted Russian Defence Ministry is saying on Tuesday.
- After a dismal 2015 of mass refugee flows, war and catastrophe, leading U.N. agencies and their partners announced last week that they are seeking over $20 billion in funding next year.
- Ola, which competed with the likes of Uber and Meru in India, connects drivers to prospective riders using its technology platform.
- Among the heart-warming stories to has emerged from the Chennai floods is a cleaning drive undertaken by a Muslim organization.
- The voice had to be listened to, not only in account of its form but for the matter which it delivered.
Seating Arrangement Questions Asked in SBI PO Prelims Set – 3
8 people A – H are sitting in a straight line all are facing north they have birthday on different dates 5,6,7,10,11,12,14,18, but not necessarily in the same order.
A sitting second to the right of D, who has birthday on 5th, A is at at the corner of the row, those who are at the corner they have birthday on odd numbered dates. C is sitting fifth to the right of E. The one who has birthday on 10th is on the immediate right of D. There are only person b/w F and G, but F is not an immediate neighbour of E. The one who has birthday on 18th. F has birthday on 12th . The one who has birthday on 7th is not an immediate neighbour of E.
Questions asked in Puzzle Test – Set 2
There are eight persons namely A, B, C, D, E, F,G and H has born in the same month of different year i.e. 1969, 1972, 1978, 1981, 1989, 1997, 2000 and 2005. Their age are considered as on the same month of 2016.G is born in even number year, but not born in the year, which does not divisible by 4.A is 36 years old now. B is 17 year older than F, who is 8 years younger than A. There are eight year gap between age of E and age of D. H is nine year younger than C, but not born in 2005. E was born earlier than G.
Seating Arrangement Questions Asked in SBI PO Prelims Slot 1 (Courtesy: Mr. Gopinath)
8 persons M,N,O,P ,Q,R,S,W have their birthdays on 10th and 27th of four different months i.e March,April,May,June not necessarily in the same order.M has birthday on 10th of a month which is having 31 days.Only one person has birthday before N.Number of persons between M and N is one less than the number of persons between N and W. O and P were held in same month having 30 days , but not in April. R has birthday after S. Only three persons have birthday between N and Q.O was held before P. (Asked Today 1St Shift)
Comprehension questions asked in SBI PO Prelims Slot 1 (Courtesy :Mr. Gopinath)
OVER a couple of days in February, hundreds of thousands of point-of-sale printers in restaurants around the world began behaving strangely. Some churned out bizarre pictures of computers and giant robots signed, “with love from the hacker God himself”. Some informed their owners that, “YOUR PRINTER HAS BEEN PWND’D”. Some told them, “For the love of God, please close this port”. When the hacker God gave an interview to Motherboard, a technology website, he claimed to be a British secondary-school pupil by the name of “Stackoverflowin”. Annoyed by the parlous state of computer security, he had, he claimed, decided to perform a public service by demonstrating just how easy it was to seize control.
Not all hackers are so public-spirited, and 2016 was a bonanza for those who are not. In February of that year cyber-crooks stole $81m directly from the central bank of Bangladesh—and would have got away with more were it not for a crucial typo. In August America’s National Security Agency (NSA) saw its own hacking tools leaked all over the internet by a group calling themselves the Shadow Brokers. (The CIA suffered a similar indignity this March.) In October a piece of software called Mirai was used to flood Dyn, an internet infrastructure company, with so much meaningless traffic that websites such as Twitter and Reddit were made inaccessible to many users. And the hacking of the Democratic National Committee’s e-mail servers and the subsequent leaking of embarrassing communications seems to have been part of an attempt to influence the outcome of the American elections.
Away from matters of great scale and grand strategy, most hacking is either show-off vandalism or simply criminal. It is also increasingly easy. Obscure forums oil the trade in stolen credit-card details, sold in batches of thousands at a time. Data-dealers hawk “exploits”: flaws in code that allow malicious attackers to subvert systems. You can also buy “ransomware”, with which to encrypt photos and documents on victims’ computers before charging them for the key that will unscramble the data. So sophisticated are these facilitating markets that coding skills are now entirely optional. Botnets—flocks of compromised computers created by software like Mirai, which can then be used to flood websites with traffic, knocking them offline until a ransom is paid—can be rented by the hour. Just like a legitimate business, the bot-herders will, for a few dollars extra, provide technical support if anything goes wrong.
The total cost of all this hacking is anyone’s guess (most small attacks, and many big ones, go unreported). But all agree it is likely to rise, because the scope for malice is about to expand remarkably. “We are building a world-sized robot,” says Bruce Schneier, a security analyst, in the shape of the “Internet of Things”. The IoT is a buzz-phrase used to describe the computerisation of everything from cars and electricity meters to children’s toys, medical devices and light bulbs. In 2015 a group of computer-security researchers demonstrated that it was possible to take remote control of certain Jeep cars. When the Mirai malware is used to build a botnet it seeks out devices such as video recorders and webcams; the botnet for fridges is just around the corner.
Cloze Test Questions asked in SBI PO Prelims 1st Slot(Courtesy : Soundharya Nehru)
In the passage given below there are 5 blanks, each followed by a word given in bold. Even blank has four alternative words given in options (A),(B),(C) and (D). You have to tell which word will best suit the respective blank. Mark (E) as your answer if the work given in bold after the blank is your answer i.e “No change required”.
TRAVELLERS sometimes have to show their travel documents five times when (1)___ [flying] a flight: at check-in, at security, then occasionally at outbound immigration, before another check when boarding. Finally there is passport control at the destination. Each is a potential queue. So regular flyers will be interested in anything that might speed up the process.
One answer could be facial-recognition technology. In the past few weeks, a number of airports have begun to introduce a system that will (2)__ [adapt] faces, match them with electronic passport photos, and allow those passengers it (3)__ [rectifies] to skip lines.
In Tokyo, the government has been (4)__ [observing] facial-recognition technology in two airports since 2014. It hopes to introduce the system in full in time for the 2020 Tokyo Olympics. In France, Groupe ADP, which operates Charles De Gaulle airport in Paris, began testing similar software in February. Queues at the airport have doubled since new security measures were introduced after terrorist attacks in 2015; this, thinks ADP, might be one way to (5)___ [leisure] the pain. In Canada, meanwhile, plans are in place to start rolling out facial-recognition kiosks this spring. Similar trials have also been announced in Schiphol Airport in Amsterdam.
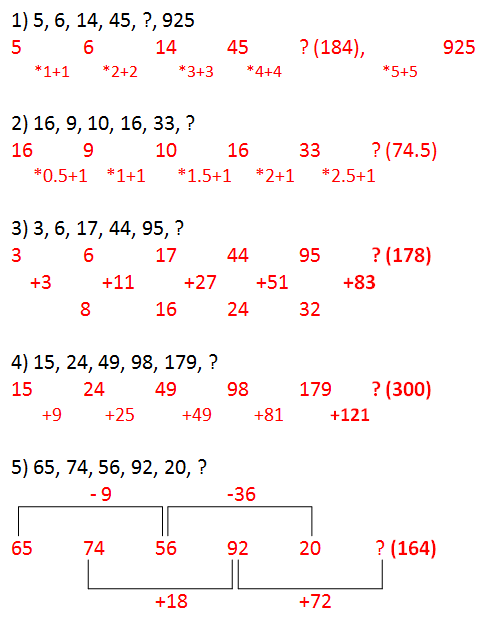
Number Series asked in SBI PO Prelims 2017 slot 1(Courtesy : Kanimozhi)
Algebra 
Quadratic Equations asked in SBI PO Prelims 2017 slot 1 : (Courtesy : Nalini)
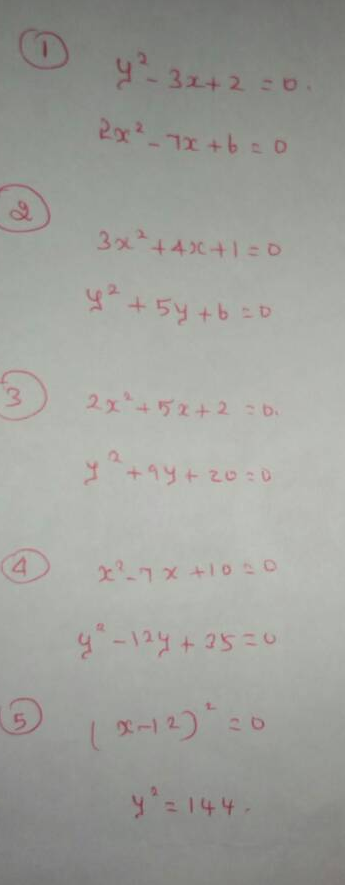
Questions asked in Slot 2
Puzzle test questions asked in SBI PO Prelims slot 2 (courtesy: Ms. Kavya)
Questions asked in Number Series – Slot 2

Questions asked in Slot 3
Questions asked in Number Series – Slot 3
Questions asked in Comprehension: Courtesy: Mr.Kavikumaran
Why everything is hackable – Computer security is broken from top to bottom
OVER a couple of days in February, hundreds of thousands of point-of-sale printers in restaurants around the world began behaving strangely. Some churned out bizarre pictures of computers and giant robots signed, “with love from the hacker God himself”. Some informed their owners that, “YOUR PRINTER HAS BEEN PWND’D”. Some told them, “For the love of God, please close this port”. When the hacker God gave an interview to Motherboard, a technology website, he claimed to be a British secondary-school pupil by the name of “Stackoverflowin”. Annoyed by the parlous state of computer security, he had, he claimed, decided to perform a public service by demonstrating just how easy it was to seize control.
Not all hackers are so public-spirited, and 2016 was a bonanza for those who are not. In February of that year cyber-crooks stole $81m directly from the central bank of Bangladesh—and would have got away with more were it not for a crucial typo. In August America’s National Security Agency (NSA) saw its own hacking tools leaked all over the internet by a group calling themselves the Shadow Brokers. (The CIA suffered a similar indignity this March.) In October a piece of software called Mirai was used to flood Dyn, an internet infrastructure company, with so much meaningless traffic that websites such as Twitter and Reddit were made inaccessible to many users. And the hacking of the Democratic National Committee’s e-mail servers and the subsequent leaking of embarrassing communications seems to have been part of an attempt to influence the outcome of the American elections.
Away from matters of great scale and grand strategy, most hacking is either show-off vandalism or simply criminal. It is also increasingly easy. Obscure forums oil the trade in stolen credit-card details, sold in batches of thousands at a time. Data-dealers hawk “exploits”: flaws in code that allow malicious attackers to subvert systems. You can also buy “ransomware”, with which to encrypt photos and documents on victims’ computers before charging them for the key that will unscramble the data. So sophisticated are these facilitating markets that coding skills are now entirely optional. Botnets—flocks of compromised computers created by software like Mirai, which can then be used to flood websites with traffic, knocking them offline until a ransom is paid—can be rented by the hour. Just like a legitimate business, the bot-herders will, for a few dollars extra, provide technical support if anything goes wrong.
The total cost of all this hacking is anyone’s guess (most small attacks, and many big ones, go unreported). But all agree it is likely to rise, because the scope for malice is about to expand remarkably. “We are building a world-sized robot,” says Bruce Schneier, a security analyst, in the shape of the “Internet of Things”. The IoT is a buzz-phrase used to describe the computerisation of everything from cars and electricity meters to children’s toys, medical devices and light bulbs. In 2015 a group of computer-security researchers demonstrated that it was possible to take remote control of certain Jeep cars. When the Mirai malware is used to build a botnet it seeks out devices such as video recorders and webcams; the botnet for fridges is just around the corner.
Not OK, computer
“The default assumption is that everything is vulnerable,” says Robert Watson, a computer scientist at the University of Cambridge. The reasons for this run deep. The vulnerabilities of computers stem from the basics of information technology, the culture of software development, the breakneck pace of online business growth, the economic incentives faced by computer firms and the divided interests of governments. The rising damage caused by computer insecurity is, however, beginning to spur companies, academics and governments into action.
Modern computer chips are typically designed by one company, manufactured by another and then mounted on circuit boards built by third parties next to other chips from yet more firms. A further firm writes the lowest-level software necessary for the computer to function at all. The operating system that lets the machine run particular programs comes from someone else. The programs themselves from someone else again. A mistake at any stage, or in the links between any two stages, can leave the entire system faulty—or vulnerable to attack.
It is not always easy to tell the difference. Peter Singer, a fellow at New America, a think-tank, tells the story of a manufacturing defect discovered in 2011 in some of the transistors which made up a chip used on American naval helicopters. Had the bug gone unspotted, it would have stopped those helicopters firing their missiles. The chips in question were, like most chips, made in China. The navy eventually concluded that the defect had been an accident, but not without giving serious thought to the idea it had been deliberate.
Most hackers lack the resources to mess around with chip design and manufacture. But they do not need them. Software offers opportunities for subversion in profusion. In 2015 Rachel Potvin, an engineer at Google, said that the company as a whole managed around 2bn lines of code across its various products. Those programs, in turn, must run on operating systems that are themselves ever more complicated. Linux, a widely used operating system, clocked in at 20.3m lines in 2015. The latest version of Microsoft’s Windows operating system is thought to be around 50m lines long. Android, the most popular smartphone operating system, is 12m.






2 comments
how many questions have you attended
Quant and aptitude fine